Difference between revisions of "Transport Canada (TC) Infrastructure Modernization - Cloud / DR / Workload Migration"
Julia.rose (talk | contribs) |
Julia.rose (talk | contribs) |
||
| Line 416: | Line 416: | ||
|'''Notes''' | |'''Notes''' | ||
|- | |- | ||
| − | | | + | |CVS |
| − | | | + | |Dev |
| | | | ||
|- | |- | ||
| Line 427: | Line 427: | ||
|DEV | |DEV | ||
|Development work in progress. | |Development work in progress. | ||
| − | |||
| − | |||
| − | |||
| − | |||
|- | |- | ||
|MMERS | |MMERS | ||
| Line 462: | Line 458: | ||
|'''Notes''' | |'''Notes''' | ||
|- | |- | ||
| − | | | + | |DB Farm |
|Up Next | |Up Next | ||
| | | | ||
| Line 470: | Line 466: | ||
| | | | ||
|- | |- | ||
| − | | | + | |SAC |
|Up Next | |Up Next | ||
| | | | ||
|- | |- | ||
| − | | | + | |Seafarer |
|Up Next | |Up Next | ||
| | | | ||
| Line 482: | Line 478: | ||
| | | | ||
|- | |- | ||
| − | | | + | |Vessel Registry |
| + | |Up Next | ||
| + | | | ||
| + | |- | ||
| + | |Web Farm | ||
|Up Next | |Up Next | ||
| | | | ||
| Line 507: | Line 507: | ||
|Deferred | |Deferred | ||
|Deferred to Phase 6. Related to COVID-19 response. | |Deferred to Phase 6. Related to COVID-19 response. | ||
| + | |- | ||
| + | |LDPS | ||
| + | |Deferred | ||
| + | |Deferred pending SCED GA. | ||
| + | |- | ||
| + | |MMEL | ||
| + | |Deferred | ||
| + | | | ||
|- | |- | ||
|PRET | |PRET | ||
Revision as of 12:44, 29 April 2021
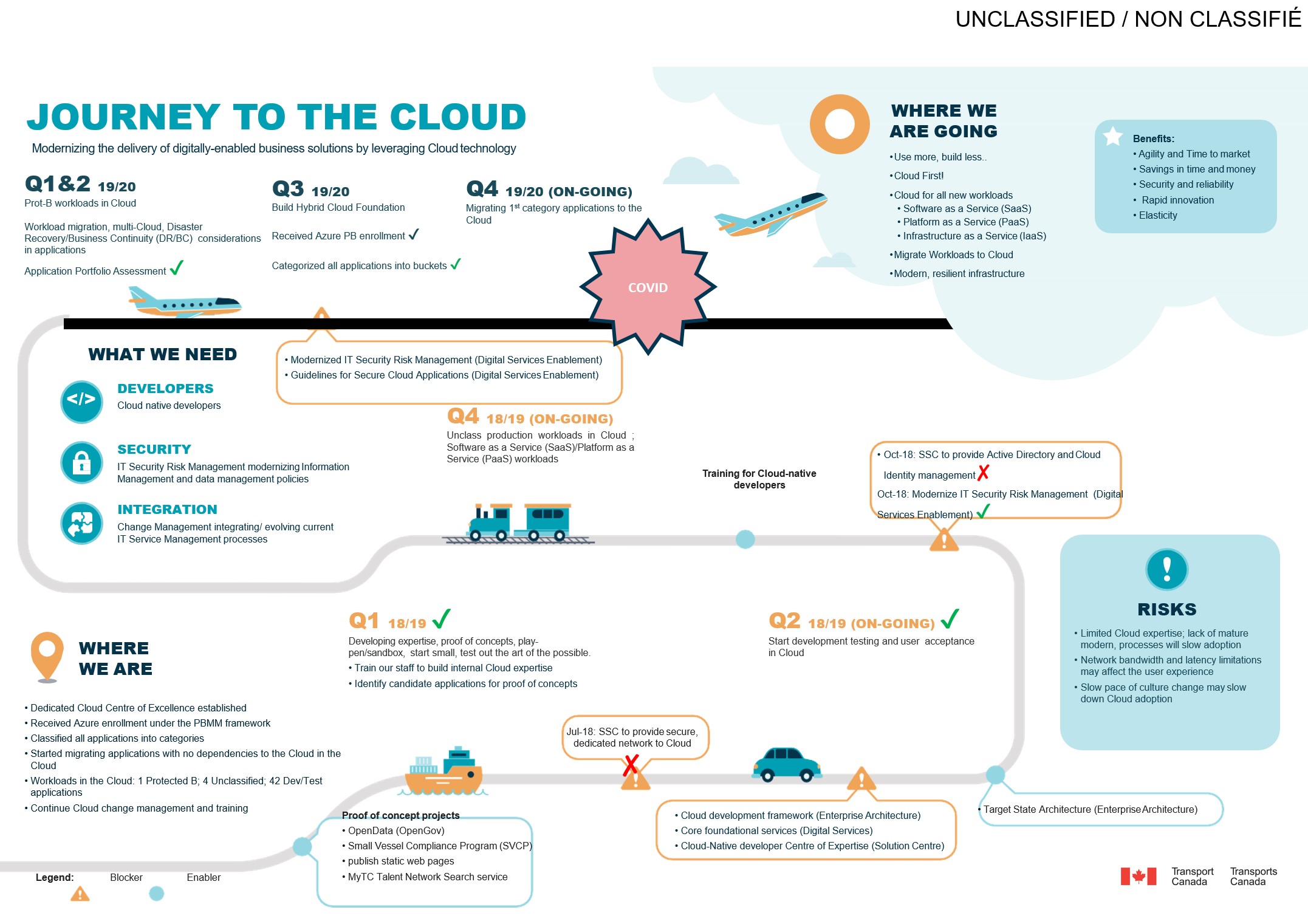
Transport Canada (TC) Infrastructure Modernization - Cloud / DR / Workload Migration[edit | edit source]
Transport Canada (TC) IT Infrastructure Modernization[edit | edit source]
The goal of this project is to deliver a complete modern infrastructure environment for TC applications in the Cloud. This requires building a foundational Cloud environment, planning and executing a workload migration plan, as well as creating and implementing a Disaster Recovery Management Program. In conjunction with SSC, a secure network to Cloud and authentication services will be established.
The Cloud will provide TC with a modern, scalable, and resilient infrastructure which offers disaster recovery and rapid time to market to support a safe, secure, efficient, and environmentally responsible transportation system in Canada.
This project is meant to address the business needs and opportunities of:
- Providing IT recovery services in the event of a disaster to ensure the delivery of critical services affecting the safety, security, and economic viability of Canadian citizens continues to operate normally.
- Responding to the Cloud First principle and direction from TBS for delivery of Digital Services.
- Responding to demands for increased IT capabilities and increased IT capacity to support TC’s programs.
- Adopting DevSecOps and modern development methodologies that are enhanced by Cloud services, such as working in Agile, Open, Collaboration.
- Implementing a Disaster Recovery Management program in response to the TBS Policy on Government Security to provide IT service continuity in a timely and efficient manner.
The key deliverables are:
- Modernized TC IT environment using Cloud solutions.
- Migration of all applications/systems within the Workload Migration (WLM) initiative to the Cloud.
- Application development and support model modernization to enable Cloud solutions providing efficiencies in delivery time and cost.
- Validated and maintained Disaster Recovery Management framework in place.
Secure Cloud Enablement and Defence (SCED)[edit | edit source]
As workloads are migrated to the Cloud, the GC perimeter shifts outside of the on-premise environment, and measures must be put in place to monitor and protect these Cloud-based environments, and respond to cyber threats quickly. The establishment of private, dedicated connections to GC approved Cloud Service Providers (CSP) will enable a hybrid IT environment, and ensure that the GC can continue to have secure access to information systems and solutions hosted in the Cloud.
Secure Cloud Enablement and Defence (SCED) is secure connectivity from Cloud to Ground that is being implemented for applications and platforms that handle Protected B data. Working with SSC, TC has implemented SCED as a pilot project for two applications: Enterprise BI and Data Analytics (eBIDA) and Policy on Government Security (PGS). eBIDA is expected to go live with SCED by February 15, 2021. The go live date for PGS is pending. SCED General Availability (GA) for all applications is expected in fall 2021.
Cloud Service Operation Model (CSOM)[edit | edit source]
The Cloud Service Operation Model (CSOM) is a framework used to assess current levels of organizational maturity in the operation, management, and governance of Cloud services. The CSOM framework and methodology is iterative and can be used for existing and new Cloud services. Microsoft performed a CSOM evaluation for TC and delivered a final report. Next steps are under review with the TC leadership team.
Project Status[edit | edit source]
This project is using Agile methodology and is in Phase 3, Launch/Execution & Control, of the TC Project Management Framework 4 Gate Model. TC's Azure Cloud Foundational Environment has been granted Authority to Operate (ATO) up to Protected-B for applications not requiring secure network connectivity.
Overall, the project was impacted by the delayed SSC delivery of SCED (Secure Cloud Enablement & Defence), required for applications that need secure connectivity, but is now moving forward with a SCED pilot for two COVID-19 related applications: PGS and eBIDA. Applications related to the COVID-19 response have been given top priority for migration, so more resources will be put on these, and other activities may be impacted. For PGS and eBIDA, resources from Solutions Centre and Microsoft have been secured for Cloud migration work. TC is working with SSC to pilot SSC's Cloud Operating Model, using DevSecOps.
Disaster Recovery (DR) plans are implemented for each application that moves to the Cloud, if required. The full DR program is expected to be set up and operational by the end of the calendar year 2022. All applications are expected to be in the Cloud, with DR plans if required, by March 2023.
| Milestones | Initial Target Completion Date | Forecast Completion Date | Actual Completion Date | Comments |
| Project Kickoff | 2017-10-26 | 2017-10-26 | 2017-10-26 | Complete: Project started on 2017-10-26. |
| Discovery & Analysis for Disaster Recovery (DR) | 2018-10-05 | 2018-10-05 | 2018-10-05 | Complete: Initial research for establishing a Disaster Recovery Program for TC. |
| Gate 0 Phase 1: Discovery and Initial Cloud Foundation | 2019-04-29 | 2019-04-01 | 2019-04-01 | Complete: Task awarded to Microsoft to collect information and create Cloud environment for TC applications. |
| Gate 1 Phase 2: Application Target State Assessment | 2019-09-20 | 2019-09-20 | 2019-09-20 | Complete: All business systems assessed and assigned a Cloud target state. |
| Cloud Foundation Build | 2019-04-01 | 2019-10-18 | 2019-10-18 | Complete: Cloud working environment for TC applications and platforms. |
| Gate 2 Project Execution Approval (under the PMF 4 Gate Model) | 2020-03-01 | 2020-03-01 | 2020-01-30 | Complete: Approval received for project execution. |
| Secure Cloud Enablement Defence (SCED) Implemented | 2018-07-16 | 2021-02-08 | 2021-02-08 | SCED implemented in pilot project. General Availability (GA) is expected in fall 2021. |
| Scrum Phase 5 Sprints | 2021-03-02 | 2021-03-02 | 2021-03-02 | New apps for this phase include CSV, MMEL, LDPS, myTC, and TMSA (CSRM), as well as remaining apps from previous phases. |
| Scrum Phase 6 Sprints | 2021-07-09 | 2021-07-09 | New apps for this phase include the COVID priority apps eGIS, ECATS, TCOMS, RAP COE, Blu Prism, TSCM, and GC Docs, as well as remaining apps from previous phases. | |
| Migration Complete for All Applications/Platforms | 2022-12-09 | 2022-12-09 | ||
| Full DR Implementation, Test, Analysis and Recommended Action Plan | 2023-03-31 | 2023-03-31 | ||
| DR Policy, Master Plan, and Framework Development and Approval | 2023-03-31 | 2023-03-31 | ||
| Gate 3 - Project Completion Date - Approval for Project Close | 2023-03-31 | 2023-03-31 | ||
| Gate 4 - Project Close | 2023-04-15 | 2023-04-15 |
Key Accomplishments[edit | edit source]
- Completed Oracle OCI Proof of Concept and procured Oracle OCI credits to be used for migration.
- Aligned TC's AWS solution to GC standards (GC PBMM Accelerator) to better position TC for enabling SCED in AWS.
- Fortinet and FortiAnalyzer Cloud firewalls were deployed for the project, enabling foundational security measures for SCED.
- TC-SSC ADM Cloud Steering Committee created to address issues and risks associated with this project.
- SCED pilot in progress for PGS and eBIDA. Planning complete and implementation phase in progress, including SSC infrastructure work.
- Applications related to COVID-19 response were prioritized and work is underway.
- Upgraded the Microsoft Multi-Factor Authentication (MFA) and Self-Service Password Reset (SSPR) features to use a centralized portal.
- Created a Cloud Migration Checklist for teams to use for migrating their apps to the Cloud.
- Created a Cloud Workload Prioritization framework to establish a priority order for applications moving to the Cloud.
- Created an Application Gateway script that dramatically reduces the amount of time required to create and configure subdomains on the network. As a manual process, creating and configuring subdomains takes about 30 minutes for each one, but with the new script it takes only 2 minutes. The script contains all the accurate settings for the subdomains, which removes any chance of configuration errors, and therefore saves the team potential troubleshooting time. The script is shared in the GCAccelerators github.
- Launched an Education Initiative as a way to create and distribute content to educate other teams in TC about Cloud migration and operations. As one of the first steps in this initiative, an onboarding checklist was created to help teams understand the steps involved in their journey to the Cloud.
- Created an Assessment Scorecard as a way to assess the criticality of moving applications to the Cloud and create a priority order. This scorecard will assist ARB with a technical understanding of the applications in the migration pipeline so they can make a decision about the migration priority order.
- All active TC employees (7,079) have been on-boarded to MS Teams.
- Active Directory Federation Services (ADFS) is now available for Cloud-based applications at TC. ADFS provides users with single sign-on capabilities by establishing a link between TC’s Azure Active Directory and the on-premise Active Directory. This reduces the amount of usernames and passwords required to log on to Cloud-based applications.
- TC and TBS have signed a Memorandum of Understanding (MoU) to fund Cloud Migration activities.
- Completed implementation of security controls required for Protected-B Cloud environment.
- Completed assessment of TC's applications for readiness to be migrated to the Cloud.
- Contracted industry Cloud expertise to assist to create, configure, and train TC FTE staff.
- Established the foundational Cloud environment, Hybrid Cloud Management (HCM), to start accepting workloads.
- As part of Culture change to adopt Cloud, 37 (formal and informal) Training sessions, 11 Technical Talks, 33 Awareness building roadshows, and four TC-wide Cloud engagement sessions have been completed.
- TC is sharing with other GC Agencies and Departments the Azure Network Template Generator via the GitHub repository.
- Began implementing DevSecOps methodology for this project.
- Dedicated TC Cloud Centre of Excellence (#TC3OE) has been established.
Overview of Transport Canada’s Cloud Centre of Excellence (#TC3OE)[edit | edit source]
TC3OE is Transport Canada’s Cloud Centre of Excellence. The TC3oE team is enabling the delivery of modern digital solutions by leveraging the Agility, Flexibility, Elasticity, and Disaster Recovery features of Cloud technologies. The team supports and maintains the Cloud foundational infrastructure, and aids designers in the planning, procurement, configuration and integration of Cloud services, so that TC clients can quickly address their rapidly changing business needs.
#TC3OE can be contacted via email at: TC.Cloud-Infonuagique.TC@tc.gc.ca
Here is a photo of our outstanding team!
Challenges: Risks and Issues[edit | edit source]
| RISK | If the SCED re-architecture goes ahead, then SCED implementation for 370+ other applications/platforms by March 2023 may be delayed. |
| Impact | High |
| Probability | Medium |
| Mitigation | Ongoing assessment of project schedule as SCED implementation develops, and continue to migrate non-SCED dependent apps. |
| RISK | If net new applications/platforms are added to project scope, then work on other priority applications/platforms must stop, negatively impacting the project schedule. |
| Impact | Medium |
| Probability | Medium |
| Mitigation | Assess and prioritize new applications/platforms and adjust project schedule accordingly. Submit change request if end date of project needs to move. |
| RISK | If there is not enough Cloud expertise and capacity on application/platform teams, then workload migration to the Cloud stalls, delaying the project schedule. |
| Impact | High |
| Probability | Medium |
| Mitigation | Engage each application/platform team early in the process, secure temporary Cloud expertise - in part by gaining resourcing through TBS, and escalate accordingly if there is not enough capacity. |
| ISSUE | The team has recently lost two resources, who were the only automation resources, which means the team is currently unable to deliver on its planned workload migration schedule. |
| Impact | High |
| Resolution Plan | Escalate to executive team to secure necessary resources and re-prioritize workload. |
| ISSUE | Identify critical success factors to prioritize workload then communicate new direction to all key stakeholders. |
| Impact | High |
| Resolution Plan | Create and implement stakeholder engagement plan. |
| ISSUE | Ongoing application assessments show that teams with applications/systems dependent on SCED/Oracle DBs are choosing not to prepare for migration at this time, causing significant delays to the migration schedule. |
| Impact | High |
| Resolution Plan | Acquire OCI to provide Oracle solutions in the Cloud, and continue to use the Application Prioritization Framework to assess readiness for migration. |
Guidance and Documentation[edit | edit source]
- Frequently Asked Questions
- GC Cloud Adoption Strategy
- Journey to the Cloud
- TC Cloud Corner
- Azure Network Template Generator on GitHub
Workload Migration Categorizations (Business Applications in Scope)[edit | edit source]
Data was sourced from the previous Microsoft Assessment.
| Security Classification | No Active Directory Dependency | No Connectivity | Requires Active Directory | Requires Connectivity with EDC | SQL Database | Total |
| Unclassified | 84 | 21 | 40 | 103 | 7 | 124 |
| Protected A | 87 | 9 | 60 | 138 | 5 | 147 |
| Protected B | 46 | 8 | 9 | 47 | 4 | 55 |
| Total | 217 | 38 | 109 | 288 | 16 | 326 |
Application Workload Migration via Agile Sprints[edit | edit source]
This project is following an iterative Agile process to migrate applications to the Cloud.
| App/Platform State | Description |
| Not Started | Work has not yet started on migrating the app/platform to Cloud. |
| Planning | Initial planning underway to determine timeframe for migrating app/platform to Cloud. |
| DEV | Development work in progress. |
| UAT | User Acceptance Testing. App/platform is undergoing testing to prepare for moving to PROD. |
| PROD/DR | Production and Disaster Recovery testing. App/platform is in the PROD environment and ready for review, testing, and cutover to Cloud. |
| Up Next | App/platform is next in line for migration. |
| Deferred | App/platform is on hold until a future date. |
| Apps/Platforms In Production | Current State | Notes |
| Alexa Recalls | PROD | |
| ASD | PROD | |
| eBIDA | PROD | Related to COVID-19 response. Part of SCED pilot. |
| CARS Exemption | PROD | Migrated to Cloud February 19, 2021. SSC COM pilot project successfully completed. |
| EGIS | PROD | |
| iServer | PROD | |
| MEDV | PROD | |
| Navigable Waters Act Registry | PROD | |
| NWAR-ESS | PROD | |
| Open Data | PROD | |
| PGS | PROD | Related to COVID-19 response. Part of SCED pilot. |
| SRF | PROD | |
| TCLR | PROD | |
| TC Search | PROD | |
| TC WWW | PROD | |
| TMSA | PROD |
| Apps/Platforms In Progress | Current State | Notes |
| CVS | Dev | |
| LDPS | Planning | |
| MISS | DEV | Development work in progress. |
| MMERS | DEV | Development work in progress. |
| myTC | Planning | |
| PRET | DEV | Development work in progress. |
| SAP BI | UAT | Dependent on SCED. |
| TEAMMATE | UAT | Performance testing in progress. |
| ZAMMAD | DEV | Development work in progress. |
| Apps/Platforms Up Next | Current State | Notes |
| DB Farm | Up Next | |
| GCDOCS | Up Next | |
| SAC | Up Next | |
| Seafarer | Up Next | |
| SSCIMS | Up Next | |
| Vessel Registry | Up Next | |
| Web Farm | Up Next |
| Apps/Platforms Deferred | Current State | Notes |
| CARTES | Deferred | Lack of capacity on database team. |
| CCM | Deferred | Waiting on funding and OCI. |
| CUMULUS | Deferred | Looking for a replacement, plan to use CUMULUS until this is found. Decision needed on effort and value to complete Cloud migration. |
| ECATS | Deferred | Deferred to Phase 6. Related to COVID-19 response. |
| LDPS | Deferred | Deferred pending SCED GA. |
| MMEL | Deferred | |
| PRET | Deferred | Lack of capacity on database team. |
| PWS (BC) | Deferred | Lack of capacity on database team. |
| RPA CoE Blue Prism | Deferred | Deferred to Phase 6. Related to COVID-19 response. Dependent on SCED. |
| RPA CoE UI Path | Deferred | Deferred to Phase 6. Related to COVID-19 response. Dependent on SCED. |
| TCOMS | Deferred | Deferred to Phase 6. Related to COVID-19 response. |
| TO_LAND | Deferred | Lack of capacity on database team. |
| TSCM | Deferred | Related to COVID-19 response. Investigating the possibility of not migrating the current application and instead, building a new one in the Cloud. |
| Vessel Registry | Deferred | Investigating the possibility of not migrating the current application and instead, building a new one in the Cloud. |
| Apps/Platforms in Pipeline | Current State | Notes |
| BALLAST INTERVENTIONS | Not Started | |
| BASE NAVIRES | Not Started | |
| CVSA | Not Started | |
| Digital Signatures | N/A | Related to COVID-19 response. No need for migration. This is a SaaS application so it's already using Cloud. |
| FORMATION | Not Started | |
| FORMATION_WEB | Not Started | |
| INC_POLL 2014 | Not Started | |
| MTCO-SMTC | Not Started | |
| PROFIL-FORMNAX | Not Started | |
| PROJETCERTI | Not Started | |
| QAIMS | Not Started | |
| SIVP-VISP | Not Started | |
| TRAVERSES | Not Started |
Business Drivers and Timeline for TC's Journey to the Cloud[edit | edit source]