Application Modernization
Note: We are continuously improving this site and information is published as we receive it. Templates and discussions related to Application Modernization can be found in the GCCollab Core Technologies group. It is recommended you join that group to watch for updates.
Check out What's New and the Discussion tab above for the latest updates !
Background[edit | edit source]
From Budget 2018:
"$110 million over six years, starting in 2018–19, to be accessed by Shared Services Canada’s partner departments and agencies to help them migrate their applications from older data centres into more secure modern data centres or cloud solutions."
Application Modernization is one of four pillars of the Workload Migration & Cloud Enablement (WLM&CE) initiative.
Overview[edit | edit source]
This handbook is meant to help departments navigate the Application Modernization Investment Framework; and other topic of interest:
- Prioritizing at-risk technologies
- Engaging with partner departments
- Performing an analysis of departmental application portfolios
- Planning for addressing the at-risk technologies through modernization
- Governance gating for endorsing modernization/migration plan and making the associated funds available
- Ongoing monitoring of status
The Investment Frame work consists of two gates:
Gate 1: a scope of at-risk technologies has been identified and approved by governance for modernization or decommissioning
Gate 2: a department's plan for modernization is ready to be endorsed by governance thus authorizing the release of Application Modernization funds.
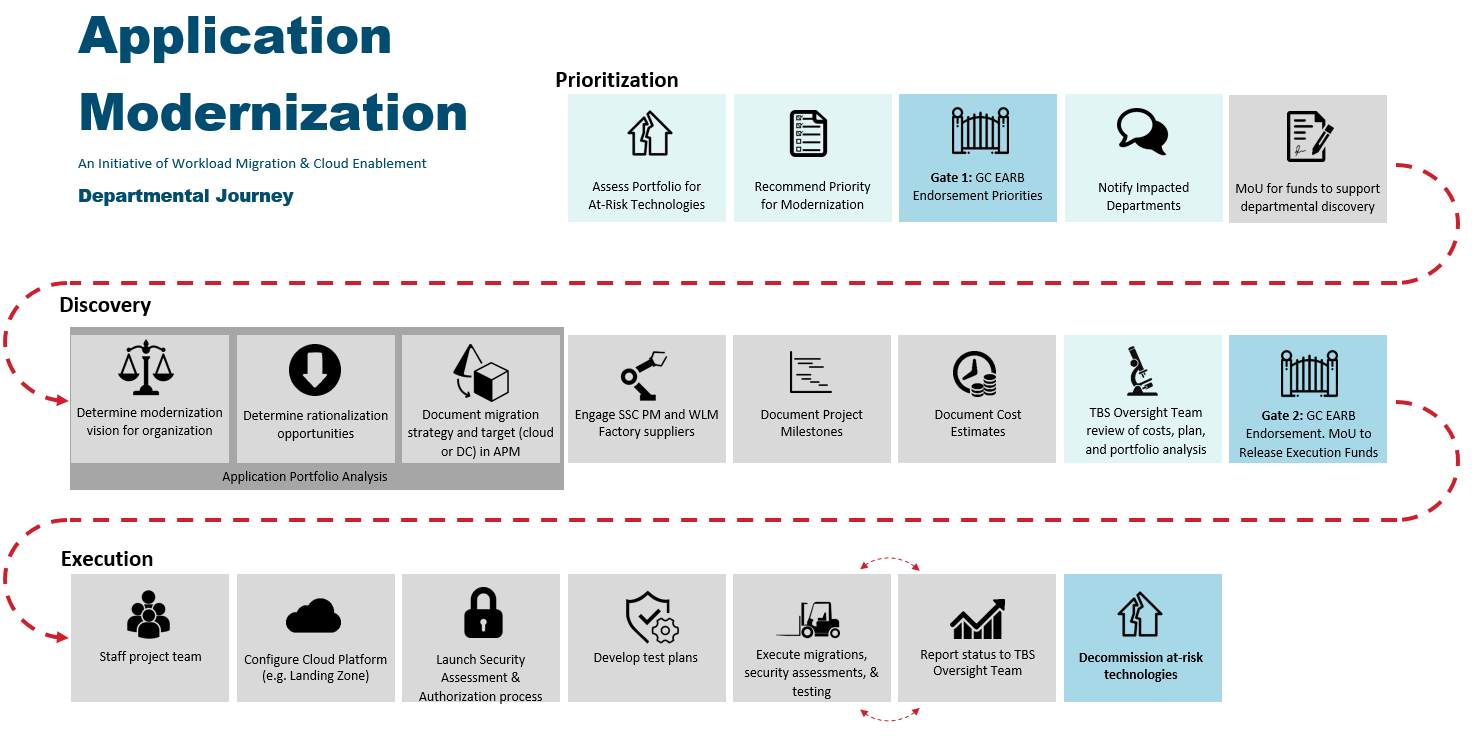
The Investment Framework also consists of four phases:
Prioritization: priorities for modernizing at-risk technologies are selected and endorsed by governance.
Engagement: notify impacted departments, distribute templates to capture technical details, modernization/migration strategies, and costing details.
Discovery: departments analyze their application portfolios to determine their strategies for modernizing at-risk technologies including a plan and cost estimates.
Execution: departments work with their partners to execute the modernization strategies identified during the discovery phase.
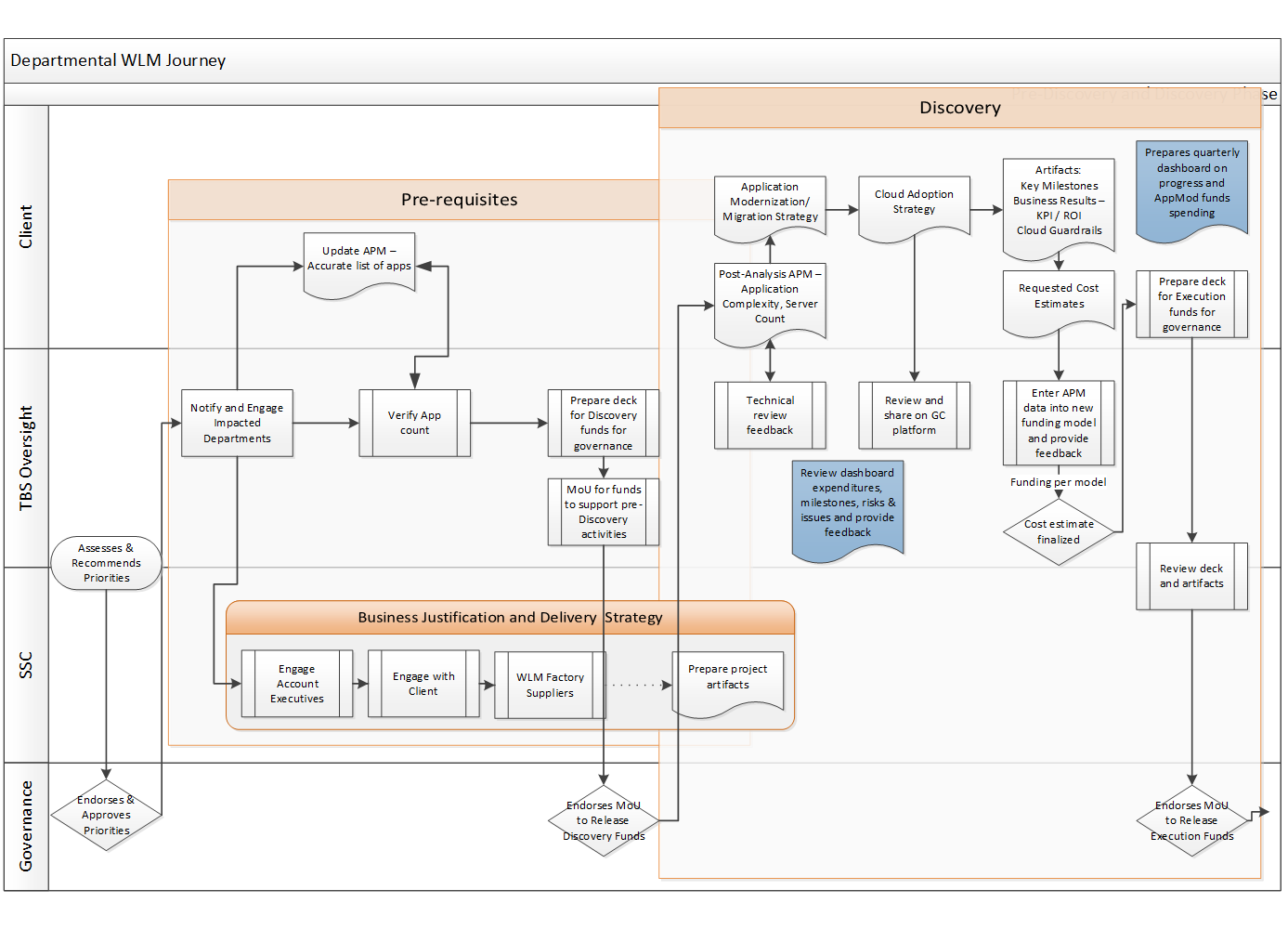
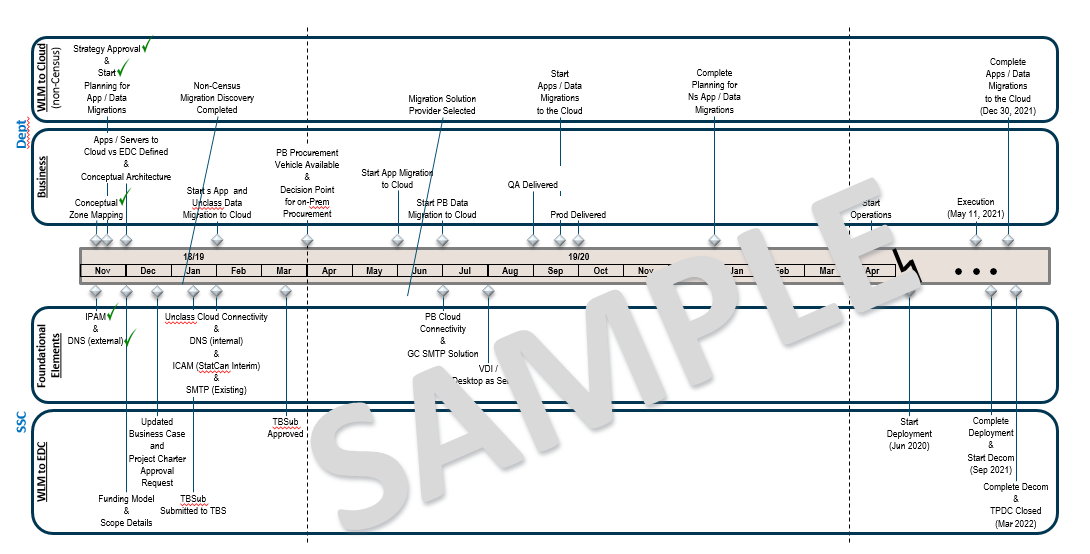
A department's journey through the Investment Framework, or can also be found here in downloadable document form.
Please review the brief Frequently Asked Questions FAQ.
Prioritization[edit | edit source]
Priorities for investment from the Application Modernization and Workload Migration funds are based upon identifying high business value applications that are impacted by at-risk technologies. These at risk technologies can include, end of life software, end of life infrastructure, outdated architectures, to be decommissioned facilities such as data centres, etc…
1) TBS and SSC are working in collaboration with GC departments that demonstrate a readiness to modernize applications and migrate them to end state hosting platforms (cloud or enterprise data centres).
2) Departments may identify applications of high business value that are impacted by technology risks as a priority investment.
If endorsed by governance, those priorities will be eligible for access to Application Modernization funds and support from the Workload Migration program. Departments are required to complete the a GCEARB Gate1 (Prioritization) template and engage your Departmental Architecture Review Board before being brought forward to request endorsement by governance:
- WLM Working group
- GC EARB
- ADM SEP
- DM CEPP
The endorsement of priority at-risk technologies must be supported by the departments’ Application Portfolio Management (APM) data, readiness to proceed with the application modernization framework, and the modernization strategy that will be used (rehost, replatform, refactor, replace and to which hosting platform; data centre or cloud services)
In 2018, the following data centre facilities were identified as at-risk technologies to be decommissioned and the applications to be migrated or modernized to a new enterprise data centre or cloud services. The first wave of workload migration projects began in 2018 and the second wave began in 2019:
| Wave | Department | Discovery | Execution |
|---|---|---|---|
| 1 | Statistics Canada 1 | X | |
| 1 | Treasury Board of Canada Secretariat 1 | X | |
| 1 | Canada Border Services Agency | X | X |
| 1 | Canada Revenue Agency | X | X |
| 1 | Department of National Defense | X | |
| 1 | Environment and Climate Change Canada | X | |
| 1 | Natural Resources Canada | X | X |
| 1 | Royal Canadian Mounted Police | X | |
| 2 | Canadian Food Inspection Agency | X | |
| 2 | Correctional Services Canada | X | X |
| 2 | Employment and Social Development Canada | X | |
| 2 | Global Affairs Canada | X | X |
| 2 | Health Canada | X | |
| 2 | Innovation, Science and Economic Development | X | X |
| 2 | Privy Council Office | X | X |
| 2 | Public Health Agency Canada | X | |
| 2 | Public Services and Procurement Canada | X | |
| 2 | Transport Canada | X |
1Pathfinder
Engagement[edit | edit source]
Once priorities are reached and departments are notified, the TBS-OCIO project manager will provide guidance and tools to start the department's journey.
- FAQ
- GC EARB Gate 1 (Discovery) template
- Departmental & Data Centre View dashboard
- Business case template.
partner departments are provided guidance/assistance to provide an accurate list of applications by updating the APM and to prepare for the governance endorsement.
- WLM Working group
- GC EARB
- ADM SEP
- DM CEPP)
Once endorsed, the Chief Information Officer of Canada (GC CIO) and the Deputy Head of a department signs the Memorandum of Understanding.
Discovery[edit | edit source]
Application Portfolio Analysis[edit | edit source]
The next three steps are an opportunity for your departments to assess its portfolio of applications and document your decisions as to how you will reduce, sustain, and modernize that portfolio.
Determine Modernization Vision for the Organization[edit | edit source]
This is an opportunity to determine the direction for the organization and ensure those performing the subsequent portfolio analysis steps understand the vision to modernize and be more transformative! Perhaps your organization has already begun a modernization journey. In today's IT environment cloud technologies combined with DevOps methods are having a large impact on how IT is delivered. Amongst the goals of these technologies and methods is to decrease lead time and time to market; in summary:
- Deliver IT faster
- Increase reliability
- Increase security
- Increase quality
These changes can be wide sweeping impacting roles, responsibilities, and culture. They are not undertaken in a year, but instead must be seen as a journey of maturity and continuous improvement. While some organizations have started this journey years ago and are ready to go "all in" on cloud and the workforce are DevOps practitioners, others have not begun the journey.
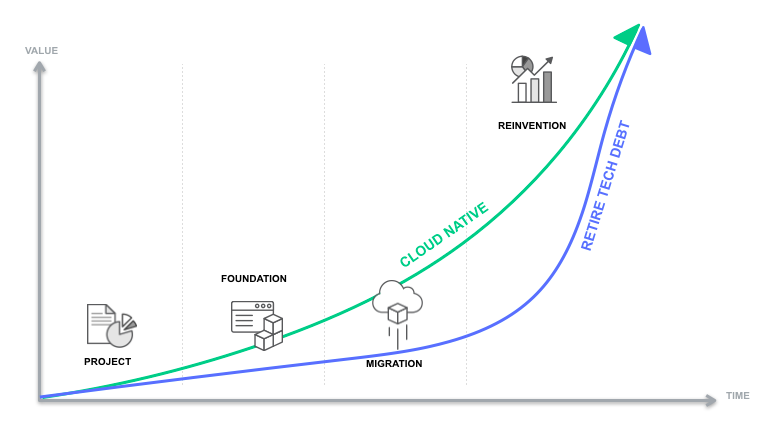
Here is a simple visual for plotting your cloud adoption .
Start small with a few low risk applications. A team of developers from within your existing workforce would lead an initiative to migrate those low risk workloads to the cloud. The build from these experiences and transfer these skills to train others. As the number of workloads grow, the need for more sophisticated methods such as automation and DevOps will need to be applied. This will facilitate scaling without impacting agility. Existing governance and roles will also need to evolve. Review the GC Cloud R&R Matrix to ensure your organization is ready to undertake the required roles to support cloud services.
See the simple cloud fitness scorecard to assess low risk workloads for cloud migration. It provides a short list to help with the decision as to where to start and to identify low risk and low effort migrations. Any application can be migrated to the cloud with enough time and effort.
Determine Rationalization and Retirement Opportunities[edit | edit source]
By the end of this step you will have assessed your portfolio and infrastructure for rationalization and retirement opportunities.
Obsolete Repositories[edit | edit source]
There are GC applications – content management systems / web-database systems - that are no longer actively used but maintained because they may contain information that might be required in the future e.g. to respond to an ATIP request.
- Departments should have an active Information Management (IM) function that can verify the actual data retention requirements applicable to a specific application.
- Departments should recognize the cost of unnecessary data retention and actively dispose of data that has been deemed unnecessary. Unnecessary data is both a cost and a liability.
Obsolete Applications[edit | edit source]
Your application portfolio rates the business value of applications. Review low business value applications. Assess whether these applications are still needed:
- Use access/update logs to identify applications that have received few updates in the past two years.
- Identify the most recent users and inquire as to the business value of the application.
Document Migration Strategy and Targets[edit | edit source]
By the end of this step you will have analyzed your portfolio of applications, updated key data in APM, chose the migration strategy for each application (one of the 5 Rs), and the target for each application (cloud or EDC).
Choose the Appropriate Migration Strategy[edit | edit source]
For each application you need to determine you migration strategy (aka the 5Rs).
| Strategy | Alternative Name | Full Description | Data Centre | Cloud |
|---|---|---|---|---|
| Retire | Decomission | Retire, decommission, sunset application. Eliminate it from the portfolio. | ||
| Rehost | Lift and shift | Redeploy applications to a different hardware environment and change the application’s infrastructure configuration. Also called Lift-and-shift. Move the solution as is, or with minor changes, to a new hosting environment (small investment of resources). | X | X |
| Replatform | Lift, shift, and tinker | Change OS / Middleware. Requiring some level of application change (medium investment of resources to change). | X1 | X |
| Refactor | Re-architect | Application will be redesigned. Sections of the application will be re-written for improvement/optimization purposes (medium to large investment of resources to change). | X | |
| Replace | Repurchase | Replace application's functionality by a new solution acquired or developed by department (medium to large investment of resources). The application will be decommissioned once replaced. | X |
1Appropriate when addressing end of life OSes
Rehost (lift and shift)[edit | edit source]
With a rehost migration strategy, the application undergoes no changes and is migrated as-is to a new data centre or cloud. This is the simplest and least effort migration strategy.
For workloads migrating to cloud, it is strongly advised that the resources (network, compute, storage) be optimized and reduced to the smallest size possible. Additionally using reserved instances for production workloads and turning off unused servers during off-hours will help ensure a lower monthly bill from your cloud provider.
Replatform (lift, shift, and tinker)[edit | edit source]
With a replatform strategy, the application undergoes minor changes as it is migrated to a new data centre or cloud. Replatforming strategies may include, but as not limited to:
- Addressing end of life (EOL) software such as those deprecated by IT Policy Implementation Notice ITPINs
- Moving to Platform-as-a-Service (PaaS) for commoditized services such as databases, web servers, file servers, container orchestration, moving to a PaaS allows for a serverless architecture.
A serverless architecture negates the need to manage and patch operating systems, middleware and manage server instances. This also reduces an organization's IT Lifecycle Management burden. Users sometimes worry that using PaaS will cause vendor lock-in. By using PaaS that have alternatives elsewhere in the market will avoid lock-in. Being able to extract your business data and business rules from a PaaS is key to avoiding lock-in. Most cloud providers offer database, web server, and file server platforms. While migrating from one to another may not be completely painless, migration tools and APIs exist to allow for this possibility.
Containers is an increasingly popular method to deploy applications. If your application is stateless, moving it to a container will not only help portability, but also help with your organization's adoption of DevOps practices.
Refactor (Re-Architect)[edit | edit source]
Refactoring is the most costly and time consuming of all strategies. This is an opportunity to take full advantage of cloud-native architectures by introducing elastic scaling of resources.
Adding disaster recover capabilities is other option for refactoring.
Migrating away from less common OSes such AIX, UNIX, or Solaris may require extensive changes to the application.
Due to the high cost of refactoring, this strategy should only be applied to high business value applications.
Replace (Repurchase)[edit | edit source]
This is an opportunity to determine if Software-as-a-Service (SaaS) solutions for some of the COTS or custom built application you may have running today. Migrating to SaaS is an opportunity to access the latest version of that service and to lower lifecycle management burden. For example, if you operate a legacy email application, you may want to take the opportunity to replace it with Office 365.
Choose Your Migration Target[edit | edit source]
Choose the target, or where the application will be migrated to, for each application.
Enterprise Data Centre (EDC): a new data centre with low technical risks
Cloud: a public cloud service provider available from the SSC GC Cloud Brokering Service
Identify Data Centre[edit | edit source]
Ensure applications are correctly allocated to its current legacy data centre. The data centre is an essential reporting dimension when TBS tracks your portfolio's progress.
Identify Mission Critical Applications[edit | edit source]
Ensure mission critical applications are correctly identified.
Identify Operating Systems[edit | edit source]
Ensure the operating systems for each application are correctly identified. This will be used to ensure all operating systems beyond end-of-life are addressed through a replatform.
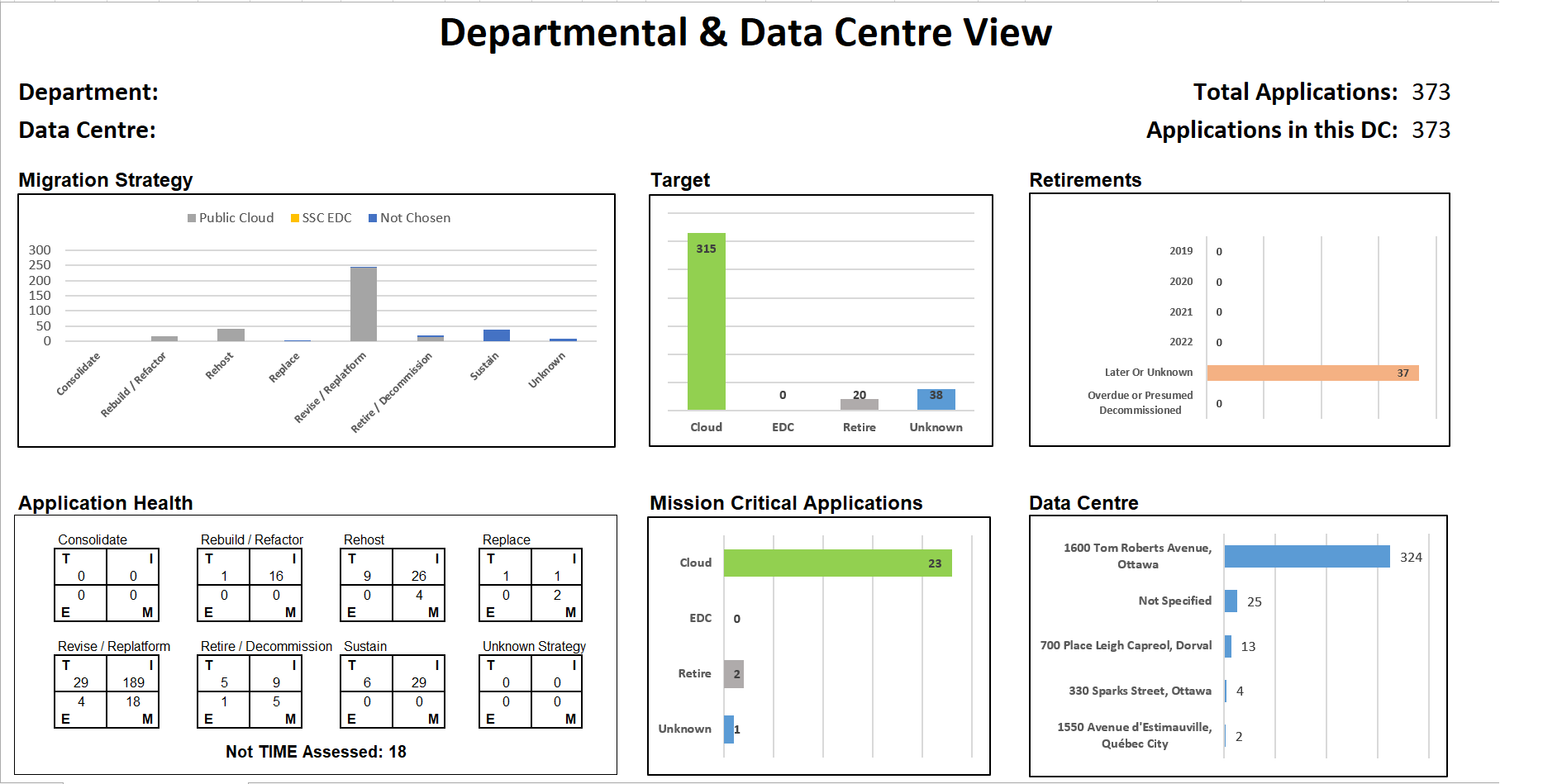
Generate Portfolio Analysis Dashboard[edit | edit source]
Request that TBS generate a dashboard of your application portfolio. This will ensure your decisions have been correctly reflected. A sample of the dashboard that is generated is found here:
Engage SSC Project Manager and WLM Factory[edit | edit source]
It is likely you have already been working with your SSC Project Manager. If not, talk to your Service Delivery Manager. At this point it would be prudent to work with a supplier qualified on the WLM Factory to help with planning and cost estimates.
Document Project Milestones (Roadmap)[edit | edit source]
Gate2: GC EARB Endorsement and MoU to Release Funds[edit | edit source]
The analysis and planning undertaken as part of the discovery phase will be presented to GC EARB to request endorsement to release the funds for the execution phase. The generic template is to be completed to present the discovery analysis and funding approval to move to the execution phase.
As part of the GC EARB, a CIO will explain their migration strategy and target choices. This includes how those choices align to the Cloud First policy (Cloud First 4.4.1.9 / Data Residency 4.4.1.10 / Non-Public Cloud GC EARB Assessments 4.1.1.2.4) of the Directive on Service and Digital. If and when endorsement is provided by GC EARB, approval will be requested from the GC CIO. A Memorandum of Understanding between the GC CIO and the deputy head of the requesting department will be agreed to by both parties.
Reporting Requirements[edit | edit source]
As per section 3: Reporting Requirements of the signed MOU between your department and TBS, the executive project dashboard is due at the end of each quarter. Please find the Quarterly Reporting Dashboard tool to be used to report the status of your modernization strategies to the TBS Oversight Team. This is a standard template that is used to monitor projects with instructions.
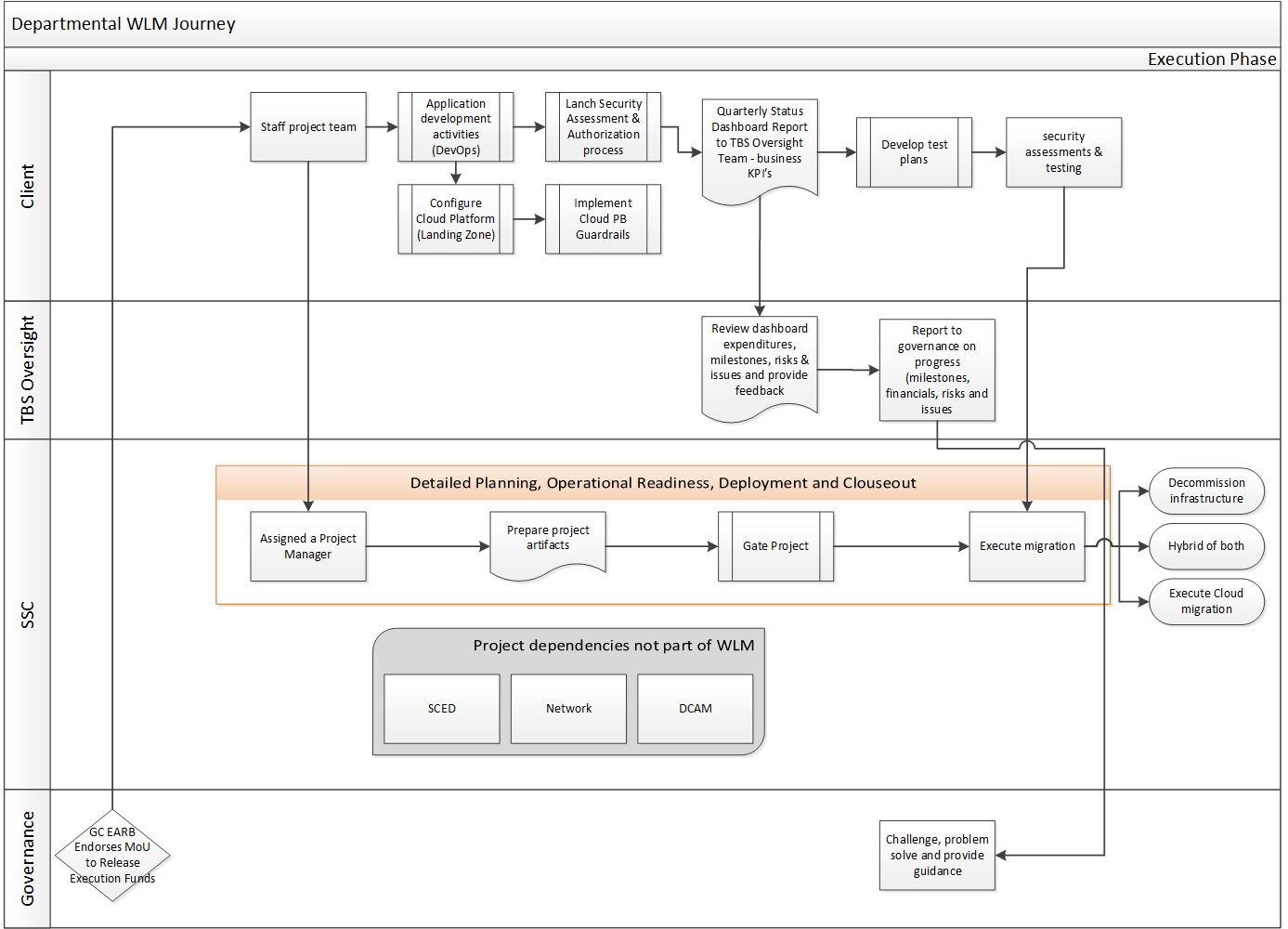
Execution[edit | edit source]
The analysis and planning undertaken as part of discovery will be presented to the governance structure as part of requesting endorsement for releasing funds for the execution phase. A new model for funding calculations is currently being developed and will be ready for utilization by the end of September 2020. A Memorandum of Understanding between the Chief Information Officer of Canada (GC CIO) and the Deputy Head of a department will be agreed upon to secure the funding.
Close Out[edit | edit source]
Lessons Learned[edit | edit source]
Change is hard. Cloud requires a major culture shift in the organization, especially in IT as it means radical transformation to some roles. Do not underestimate the fear that people will have. Organizational change management must be at the forefront.
Strong support required by deputy head and all levels of senior leadership. Due to the magnitude of change required and the underlying complexity, the senior management table MUST demonstrate consistent, strong leadership to ensure success.
Cloud is a journey, not a destination. It is very complex, and will take longer than you think. Start now, before you have all of the information. BUT – start smaller and simple, avoid serious injury when you fall. Because you will fall. Learn to crawl before trying to run. Fully embracing cloud will take years.
Partner with others. Having an integrated project team with SSC has been key success factor. Leverage the expertise of industry and of others that have gone before you.
Strong support required by deputy head and all levels of senior leadership.
Shallow pool of resources with the required expertise. Resources are routinely targeted by other departments and private sector. Ability to attract and retain talent is key, and is very challenging in public sector environment.
Products may not be as advertised. While the products may be released as GA, and have been tested on the open market, they do not necessarily function as intended. There may be a lot of back and forth with the vendor (in our case MS) in order to get the functionality you were expecting - add some contingency time to your project for this.
Voice your concerns immediately. You have to watch your costs like a hawk and have a strong understanding of what the costs should be - more importantly, you have to voice your concerns immediately to the vendor so that they can investigate and adjust. eg Log analytics
Be like water You have to work with a singular vision and purpose, but you have to be like water otherwise. The landscape in the cloud is ever changing - gone are the days of set it and forget it. Also, politically, there are always changes too - so you must be prepared to pivot when needed. eg. Pathfinder, APDC Closure, desktop, etc...
References & What's New[edit | edit source]
WHAT'S NEW[edit | edit source]
OCIO Application Portfolio Management/Aging IT Application Assessment
NEW! (Jan-2021) Visit the M365 Playbook on GCpedia
Enterprise IT Service Standards - Standard on; IT Profile, IT Entitlements, IT Service Common Configurations, Enterprise IT Service Usage Restrictions and more!
Zero Trust Security Concept PDF (Aug-2020) Zero Trust Security (Jul-2020)
FWDThinking Episode 5.2: Showing What’s Possible—an extended interview with Minister Murray
NEW! Accelerating Protected Workloads (Sept 2020)
!! TBS GC Enterprise Architecture/Enterprise Solutions
PSPC EA and GC Programs and Solutions
!! Security Playbook for Information System Solutions
The Canada School of Public Service (CSPS) Digital Academy is offering a virtual learning program: Getting Started with Cloud Computing
!! DEPARTMENTAL CLOUD STRATEGIES
Workload Migration SSC WLM Program
Gartner: Workload Placement in Hybrid IT
DPI - Charting a path to success for Workload Migration: Approaches and Best Practices
TB Policies & Standards[edit | edit source]
Directive on Service and Digital
Guidance[edit | edit source]
Government of Canada Digital Playbook (draft)
Government of Canada Cloud Adoption Strategy
Government of Canada Security Control Profile for Cloud-Based GC IT Services
Government of Canada Cloud Security Risk Management Approach and Procedures
CSE ITSG-22 Baseline Security Requirements for Network Security Zones in the Government of Canada
CSE ITSG-38 Network Security Zoning – Design Consideration for Placement of Services within Zones
CSE ITSG.30.031 V2 User Authentication Guidance for Information Technology Systems
CSE ITSG.40.062 Guidance on Securely Configuring Network Protocols
Blog[edit | edit source]
The GC Accelerators - Accelerating the Secure Adoption of Cloud Services
Part 1: Application Modernisation — Making IT Delivery Less Effort
Part 2: Application Modernisation — Understanding Modernisation Strategies
Part 3: Application Modernisation — Assessing Your Portfolio
Part 4: Application Modernisation — Choosing Your Target
Part 4 ¾: Application Modernisation – Continuous Modernisation
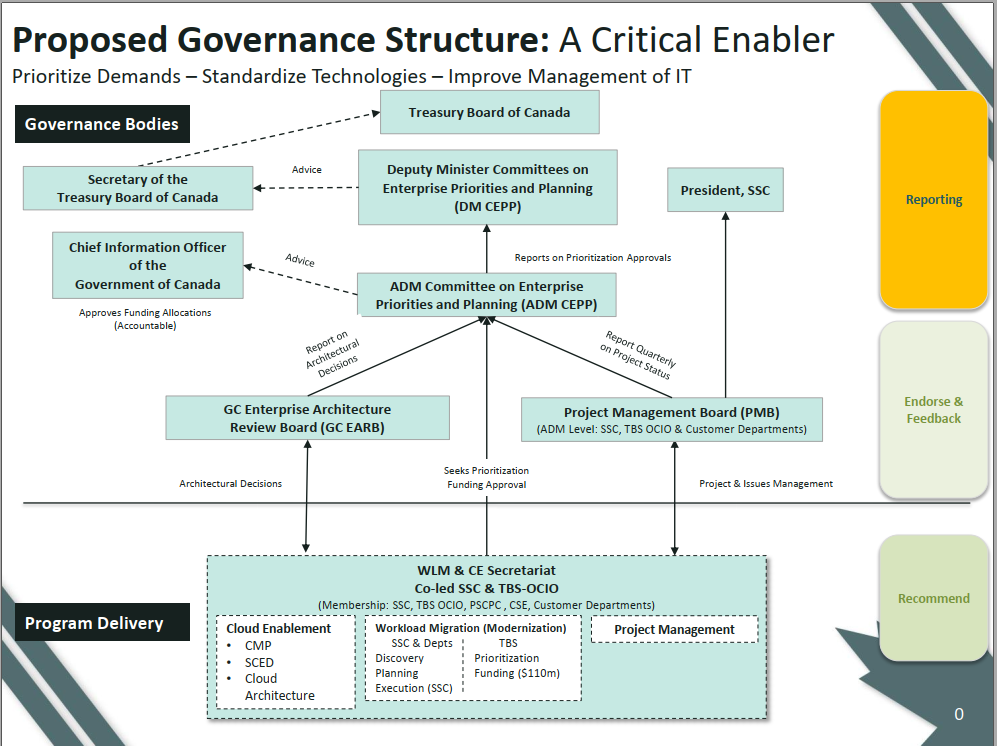
Governance[edit | edit source]
Prioritization/Endorsement critical path